Testing the Operational Effectiveness of the AML/CFT Framework
In the post-greylist environment, money laundering remains a key strategic risk. The competent authorities have upped their supervisory and enforcement game, with a total of €11.8m in administrative fines issued by the FIAU in 2021 to subject persons across all sectors. A closer look at the most common failures identified by the FIAU, highlights deficiencies in customer risk assessments (CRA) and business risk assessments (BRA), as well as the inadequacy of measures pertaining to customer verification, transaction scrutiny, purpose and intended nature, and treatment of high-risk customers. In essence, while these components may have been put in place by the subject persons, significant issues were identified when it comes to their operational effectiveness.
Indeed, operational effectiveness is fast becoming a key priority area for MLROs, senior management, audit committees and board members. While due importance should still be given to the compliance requirements that every subject person must meet, MLROs must seek to identifying weaknesses within their products, processes and tools which may be used by criminals to their advantage. Criminals are continuously seeking to develop new ways of laundering their funds, and these could render existing control frameworks obsolete. Furthermore, AML incidents put subject persons’ reputation on the line, with potentially significant impacts on the entity concerned.
The review of the AML framework may be conducted by the third line of defence. The objective here is to assess the design and operating effectiveness of the internal control framework, to provide an independent opinion thereon, and to propose recommendations on how identified weaknesses can be addressed by management. The independence of the function conducting such a review is crucial in ensuring that any opinions expressed are free from any internal and external interference, or undue pressure. Whilst preserving independence, the function undertaking the review should work with, and not against, management and the relationship should be built on mutual trust. This can be ensured by discussing findings (rated by priority) and remediation plans during the course of the review. The report is first presented to management, who are also requested to provide their input in relation to the findings, before it is presented to the Board or Audit Committee.
The effectiveness review needs to have a well-defined scope. Scoping can include focusing on the areas which pose the highest risk, such as onboarding, the application of the risk-based approach, and transaction monitoring. Such an approach would ensure value-for-money, since resources will be focused on priority areas. Another approach to the review would be to undertake a health check of the holistic control framework. the latter would be designed to provide an insight into the company’s compliance with its AML/CFT obligations, as well as a high-level overview of potential control failures.
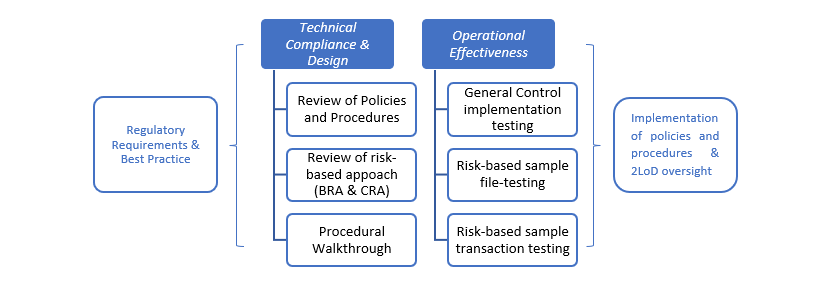
Typically, an effectiveness review can have two facets, namely the Technical Compliance & Design and the Operational Effectiveness of the control framework:
- Technical Compliance & Design: The assessment of the design of policies, procedures, controls and systems, to ensure that they meet the regulatory requirements and are in line with best practices and with the risk appetite of the company;
- Operational Effectiveness: A review of the implementation of the company’s policies and procedures by the first line of defence, to guarantee that the controls designed by management are implemented in practice, and that the controls are effective in mitigating the risk. This may also cover the oversight and checks carried out by the second line of defence, these being Compliance and MLRO. This phase will identify control failures emanating from the various components of the control framework. Various methodologies may be used during this phase, such as data analysis to provide greater coverage, which could eliminate or reduce the need for laborious substantive sampling. File testing on a sample basis could also be an option.
The following table identifies some risk-based areas that such a review can look into:
Component Samples | Technical Compliance & Design (examples of review points) | Effectiveness (examples of review points) |
CDD and Onboarding |
|
|
Customer Risk Assessment (CRA) |
|
|
Transaction Monitoring |
|
|
In conclusion, every subject person’s control framework goes through a process of evolution. In some cases this process may be more accelerated, particularly following supervisory visits or independent assessments. In spite of this, legacy issues pertaining to long-standing customers and controls may still persist and compromise the overall framework. The cross-border exposure of subject persons in Malta, albeit to different extents, also poses an additional layer of risk. An effectiveness review provides an accurate snapshot of the adequacy of the company’s control framework and ensures it is commensurate with the ML/FT risk exposure that the subject person faces.